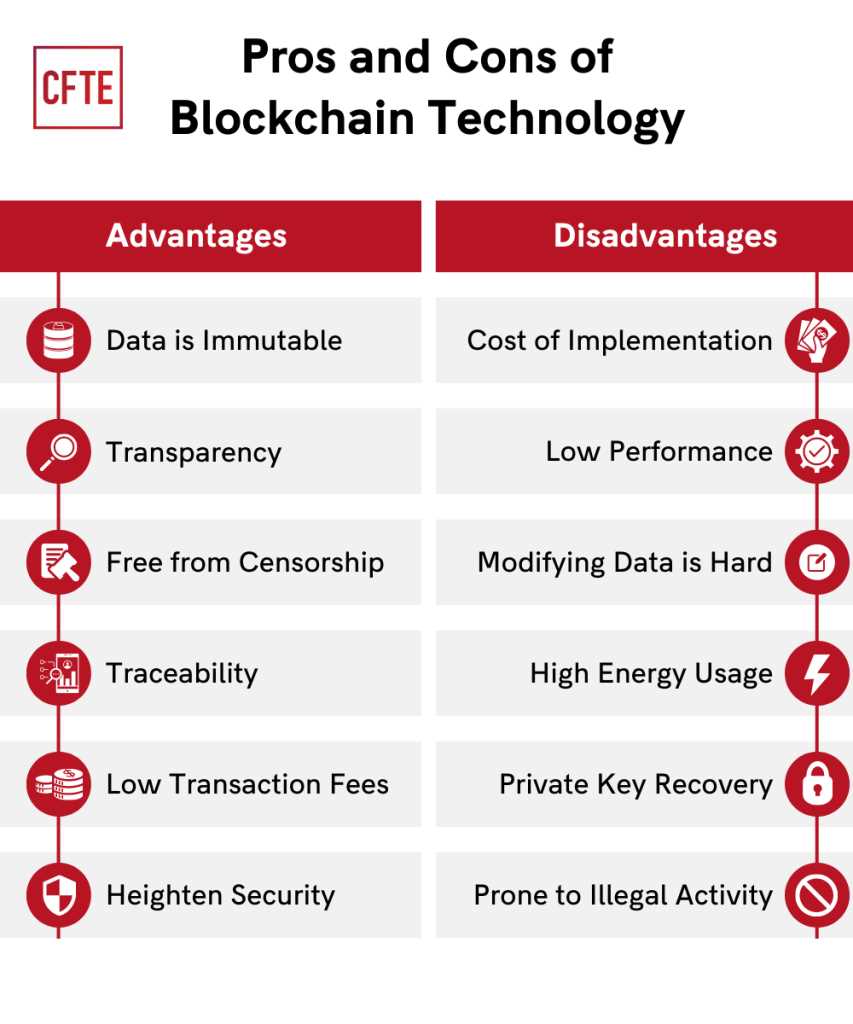
Blockchain technology has gained widespread attention and recognition for its potential to revolutionize various industries. However, like any other technological innovation, it is not without its weaknesses and limitations. Understanding these key challenges is essential for individuals and businesses considering the adoption of blockchain technology.
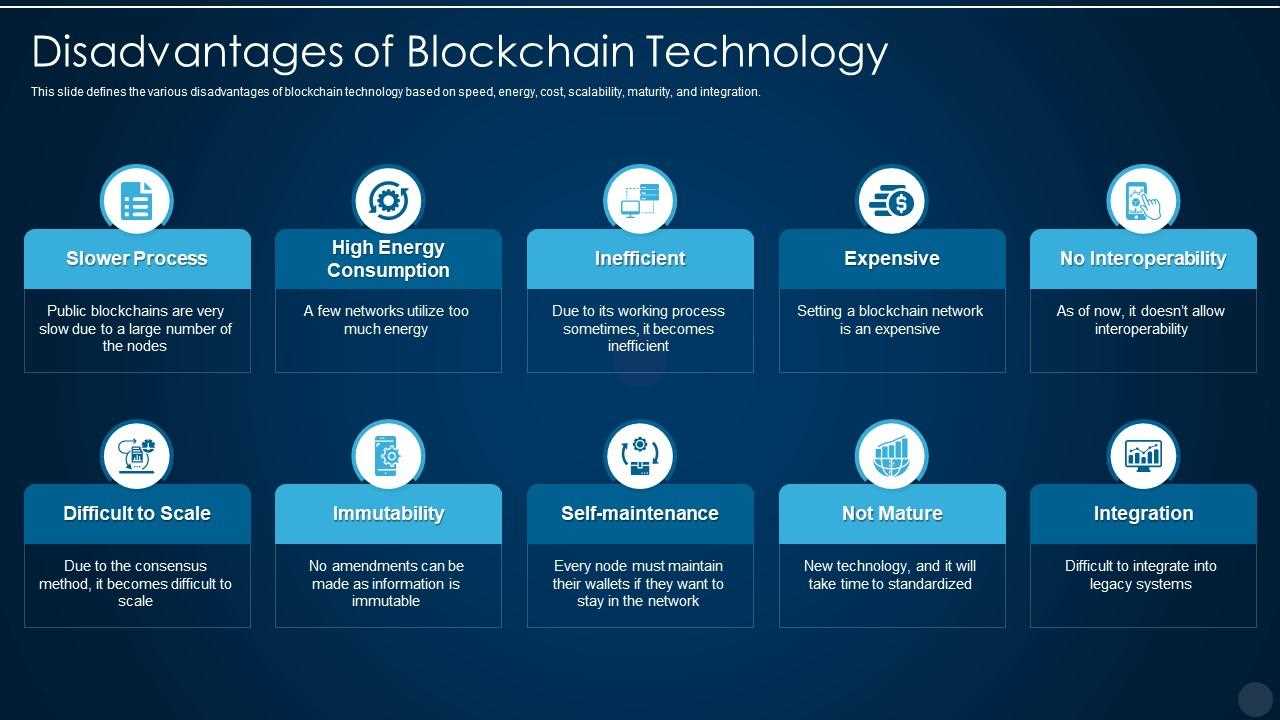
Scalability is one of the primary concerns associated with blockchain. As the number of users and transactions on a blockchain network increases, the technology struggles to handle the growing volume of data and maintain fast transaction speeds. This inherent limitation hinders its usability for large-scale applications, such as global financial systems, where high throughput and low latency are essential.
Energy Consumption is another significant drawback of blockchain technology. The process of validating transactions and adding them to the blockchain, known as mining, requires substantial computational power and energy consumption. The energy-intensive nature of blockchain networks has raised concerns about its environmental impact, particularly as cryptocurrencies become more popular.
Privacy and Security is a critical area of concern when it comes to blockchain technology. While blockchain is often touted as secure due to its decentralized and immutable nature, certain vulnerabilities exist. For example, the transparency of the blockchain can compromise the privacy of sensitive data. Moreover, the quantum computing threat looms large in the world of blockchain, as quantum computers have the potential to break current encryption algorithms and compromise the security of blockchain networks.
Scalability Challenges
While blockchain technology offers numerous advantages, it also faces significant scalability challenges. As more and more users join the network and new transactions are added, the performance of the blockchain can suffer.
One of the main scalability challenges is the limited transaction processing capacity. In most traditional blockchain systems, the number of transactions that can be processed per second is relatively low. This limitation arises because every transaction needs to be broadcasted to all the nodes in the network and validated by each of them. As the number of nodes increases, the time it takes to reach a consensus and validate transactions also increases, slowing down the overall performance.
Another scalability challenge is the size of the blockchain itself. As the number of transactions increases over time, the size of the blockchain grows exponentially. Storing and replicating such a massive amount of data can become a storage and bandwidth bottleneck, making it difficult for new nodes to join the network and slowing down the synchronization process.
Furthermore, the energy consumption required for mining and securing the blockchain also poses scalability challenges. As the blockchain grows, more and more computational power is needed to maintain its security and integrity. This can lead to an unsustainable increase in energy consumption, making the blockchain less environmentally friendly and potentially limiting its adoption at a larger scale.
To address these scalability challenges, various solutions have been proposed and implemented. These include off-chain scaling solutions like payment channels, sharding, and layer-two protocols. These solutions aim to increase the transaction processing capacity, reduce the size of the blockchain, and improve the overall scalability of the technology.
Overall, scalability remains a key weakness and limitation of blockchain technology. Although progress has been made in addressing these challenges, further innovations and improvements are still needed to make blockchain technology more scalable and efficient.
Limited Transaction Throughput
One of the key weaknesses of blockchain technology is its limited transaction throughput. In traditional centralized systems, such as credit card networks or online payment processors, thousands of transactions can be processed per second. However, blockchain technology currently lacks the scalability to compete with these systems.
The main reason for the limited transaction throughput is the consensus mechanism employed by most blockchains, such as proof-of-work. In proof-of-work, miners compete to solve complex mathematical puzzles to validate transactions and add them to the blockchain. This process takes time and requires significant computational power. As a result, the transaction processing capacity of blockchain networks is severely limited.
For example, the Bitcoin network, one of the most well-known blockchain networks, can process only about 7 transactions per second. This is in stark contrast to Visa, which can handle thousands of transactions per second. This limitation becomes a major hurdle when it comes to mass adoption of cryptocurrencies for everyday transactions.
Attempts have been made to address this limitation through various solutions, such as off-chain transactions and layer 2 scaling solutions. Off-chain transactions involve conducting transactions outside of the blockchain, reducing the burden on the main blockchain network. Layer 2 scaling solutions, such as the Lightning Network, aim to increase transaction throughput by processing transactions off-chain and only settling the final result on the main blockchain.
Despite these efforts, the limited transaction throughput remains a significant challenge for blockchain technology. Until a scalable solution is found, blockchain may struggle to compete with traditional payment systems in terms of transaction speed and efficiency.
Increased Network Latency
Network latency refers to the time it takes for data to be sent from one point to another on a network. In the case of blockchain technology, network latency can be a significant limitation.
When a transaction is made on a blockchain, it needs to be validated and added to the blockchain’s distributed ledger. This validation process involves a consensus mechanism, such as proof-of-work or proof-of-stake, where multiple nodes on the network compete to solve a complex mathematical problem.
However, this process takes time and can result in increased network latency. In a blockchain network with a large number of nodes, the validation process can be slow due to the amount of computational power required.
Moreover, in a public blockchain where anyone can participate in the validation process, the network can be crowded with numerous transactions awaiting validation. This can lead to congested network traffic and further increase the network latency.
The increased network latency in blockchain technology can impact the scalability and efficiency of the network. It can slow down transaction processing times and limit the number of transactions that can be processed within a given time frame.
To address this limitation, various solutions have been proposed, such as off-chain transactions and layer-2 protocols. These approaches aim to reduce the reliance on the main blockchain network, allowing for faster and more scalable transactions.
Security Risks
Despite its many advantages, the blockchain technology is not without its security risks. Here are some of the key security risks associated with blockchain:
1. Why is Galxe (GAL): Security risks in blockchain technology stem from vulnerabilities in the underlying code, smart contracts, and network nodes. Any weakness in the code or implementation can be exploited by attackers to gain unauthorized access or manipulate the blockchain.
2. Double Spending: Double spending is a potential security risk in blockchain networks. It refers to the ability to spend the same digital currency more than once. While blockchain technology has mechanisms in place to prevent double spending, certain attacks can exploit vulnerabilities and lead to fraudulent activities.
3. 51% Attack: A 51% attack, also known as a majority attack, occurs when an individual or organization controls more than 50% of the total computing power in a blockchain network. This allows them to manipulate transactions, reverse transactions, and double spend their digital currency. Such an attack undermines the trust and security of the blockchain network.
4. Smart Contract Risks: Smart contracts are susceptible to bugs, vulnerabilities, and coding errors. Once deployed on the blockchain, they cannot be modified or revoked, making them an attractive target for hackers. Exploiting smart contract vulnerabilities can lead to unauthorized access, manipulation, or loss of digital assets.
5. External Integration Risks: Integrating external systems or services with a blockchain network can introduce additional security risks. Weaknesses in the external systems or interfaces can be exploited to gain unauthorized access to the blockchain or compromise the integrity of the data stored on the blockchain.
It is crucial for organizations and developers to be aware of these security risks and implement robust security measures to protect their blockchain networks and assets.
% Attack Vulnerability
One of the key weaknesses of blockchain technology is its vulnerability to a % attack. In a % attack, a single entity or a group of colluding entities acquire over 50% of the total computing power of a blockchain network. Once this threshold is breached, the attacking entity can manipulate the blockchain’s decentralized consensus mechanism and potentially control the entire network.
The % attack vulnerability arises from the fundamental concept of blockchain consensus, which relies on the majority of participants acting in good faith. When a malicious entity gains majority control, it can alter the blockchain’s transaction history, double-spend coins, and even exclude transactions from being added to the blockchain. This compromises the integrity and security of the blockchain, undermining its trustworthiness.
Furthermore, the % attack vulnerability is exacerbated by the increasing centralization of mining power. As mining operations become concentrated in the hands of a few powerful entities, the risk of a % attack becomes more significant. These powerful entities have the resources to acquire a majority stake in the network’s computing power, making it easier for them to execute a successful attack.
To mitigate the % attack vulnerability, several solutions have been proposed. One approach is to encourage decentralization by promoting the participation of a larger number of nodes and miners. This would make it more difficult for any single entity to acquire majority control. Additionally, implementing consensus mechanisms that are resistant to % attacks, such as proof of stake (PoS), can provide an alternative solution.
| Weakness | Potential Impact |
|---|---|
| % Attack Vulnerability | Allows a malicious entity to manipulate the blockchain consensus and potentially control the network. |
In conclusion, the % attack vulnerability is a significant weakness of blockchain technology. It compromises the integrity and trustworthiness of the blockchain, and the increasing centralization of mining power exacerbates this vulnerability. However, through the implementation of decentralization and alternative consensus mechanisms, it is possible to mitigate the risk of % attacks and enhance the security of blockchain networks.
Smart Contract Bugs
Smart contracts are self-executing contracts that are written in code and automatically enforce the terms of the agreement. While they offer numerous benefits, such as eliminating the need for intermediaries and reducing transaction costs, they are not without their weaknesses.
One key weakness of smart contracts is the potential for bugs in the code. Smart contracts are typically written in high-level programming languages, such as Solidity for Ethereum. However, even experienced programmers can make mistakes or overlook vulnerabilities in the code. These bugs can lead to unforeseen consequences and may be exploited by malicious actors.
One common type of smart contract bug is the reentrancy bug. This occurs when a contract allows an external contract to call back into it before the first call has completed. This can result in unexpected behavior and can even allow an attacker to drain funds from the contract. The infamous DAO attack in 2016, where millions of dollars worth of cryptocurrency were stolen, was due to a reentrancy bug in a smart contract.
Another common type of bug is the overflow and underflow bug. Smart contracts often involve calculations and manipulating large numbers. If the code is not properly written to handle overflow and underflow conditions, it can lead to incorrect results or even cause the contract to become permanently locked.
Furthermore, smart contracts are immutable once deployed on the blockchain. This means that if a bug is discovered after deployment, it cannot be easily fixed or patched without creating a new contract. This lack of upgradability can be problematic if a critical bug is discovered or if the contract needs to be modified to accommodate changing requirements.
In conclusion, while smart contracts offer many benefits, they are not infallible and are susceptible to bugs. It is important for developers to thoroughly test and audit their code to minimize the risk of vulnerabilities. Additionally, ongoing research and improvements in smart contract languages and development frameworks are crucial to mitigate the impact of such bugs.
Difficulty in Identifying Participants

One of the key weaknesses of blockchain technology is the difficulty in identifying the real-world participants involved in a transaction. While blockchain provides a pseudonymous and secure way to transact digitally, it does not provide information about the real identities of the participants.
This lack of identification can be problematic in certain situations. For example, in the case of illegal activities such as money laundering or terrorist financing, it becomes challenging for law enforcement agencies to trace the individuals involved. This anonymity can thus be exploited by criminals who can use blockchain technology to carry out illicit activities without fear of being identified.
Moreover, the difficulty in identifying participants also poses challenges in terms of regulatory compliance. Many jurisdictions require businesses to know their customers and perform due diligence to prevent money laundering and financial crimes. However, with blockchain, it becomes difficult to verify the identities of the participants, thereby making it harder to comply with these regulations.
To address this issue, some blockchain platforms have started to incorporate Know Your Customer (KYC) and Anti-Money Laundering (AML) procedures. These procedures involve collecting and verifying the identity information of participants before allowing them to transact on the blockchain. While this can help in mitigating some risks, it also introduces concerns related to privacy and data security.
| Key Points |
|---|
| 1. Identifying participants in blockchain transactions is difficult due to the pseudonymous nature of the technology. |
| 2. Difficulty in identifying participants can be exploited by criminals for illegal activities. |
| 3. Lack of identification makes regulatory compliance challenging. |
| 4. Some blockchain platforms are incorporating KYC and AML procedures to address this issue. |
Energy Consumption
One of the key weaknesses and limitations of blockchain technology is its significant energy consumption. The process of verifying and validating transactions on a blockchain requires a tremendous amount of computational power, which in turn requires a substantial amount of electricity.
Blockchain networks rely on a distributed network of nodes to validate transactions and maintain the integrity of the blockchain. In order to participate in the validation process, nodes must compete to solve complex mathematical problems, a process known as mining. This competitive mining process is energy-intensive and requires powerful hardware.
Bitcoin, the most well-known blockchain-based cryptocurrency, has faced criticism for its energy consumption. The Bitcoin network consumes more electricity than some entire countries, which has led to concerns about its environmental impact.
While efforts have been made to reduce the energy consumption of blockchain technology, such as the introduction of more energy-efficient consensus algorithms, it remains a significant challenge. The energy consumption of blockchain networks is a barrier to scalability and could limit the adoption of blockchain technology in certain industries or regions where energy resources are limited or expensive.
| Energy Consumption | Solutions |
|---|---|
| High | – Introduction of more energy-efficient consensus algorithms |
| – Use of renewable energy sources for mining | |
| – Off-chain or sidechain solutions to reduce the computational load on the main blockchain |
Efforts are being made to address the energy consumption issue, but it remains an important consideration when evaluating the feasibility and sustainability of blockchain implementations.
Lack of Regulatory Framework
One of the key weaknesses and limitations of blockchain technology is the lack of a regulatory framework. As blockchain technology becomes more widely adopted and integrated into various industries, there is a growing need for clear and consistent regulations to govern its use.
Currently, there is a lack of standardized regulations for blockchain technology, which can lead to uncertainty and legal challenges. Without a regulatory framework in place, companies and individuals may be hesitant to fully embrace blockchain technology due to concerns about compliance and potential legal risks.
Additionally, the lack of a regulatory framework can hinder the widespread adoption of blockchain technology. Government entities and regulatory bodies may be reluctant to support or endorse blockchain projects without clear guidelines and oversight. This can limit the growth and development of the technology in certain regions or industries.
Furthermore, the absence of a regulatory framework can also make it difficult to address issues such as security, privacy, and consumer protection. With the decentralized and immutable nature of blockchain, it can be challenging to enforce standards and regulations that protect individuals and businesses from fraud or data breaches.
Overall, the lack of a regulatory framework for blockchain technology poses significant challenges and limitations. In order to fully realize the potential of blockchain technology and ensure its responsible and secure use, it is crucial to establish comprehensive regulations that address the unique features and challenges of this innovative technology.
Uncertainty in Legal Status

One of the key weaknesses and limitations of blockchain technology is the uncertainty surrounding its legal status. Blockchain operates across borders and jurisdictions, making it difficult to define which laws and regulations apply to its use. This ambiguity creates challenges for businesses and individuals who want to adopt blockchain technology but are unsure about its legal implications.
One area of concern is the lack of clarity regarding smart contracts. Smart contracts are self-executing contracts with the terms of the agreement directly written into code. They are a key feature of blockchain technology and provide automation and trust in transactions. However, there is a lack of legal precedents and regulations that address the enforceability of smart contracts. This uncertainty poses a risk to businesses, as they may be unsure of the legal consequences of relying on smart contracts for their operations.
Another legal concern is related to data privacy and protection. Blockchain technology is built upon the principles of transparency and immutability, which means that data recorded on the blockchain is visible to all participants and cannot be altered. While this feature provides transparency and trust, it also raises questions about data privacy and compliance with data protection laws, such as the General Data Protection Regulation (GDPR) in the European Union. Blockchain technology may face challenges in adhering to these laws, especially when personal data is involved.
Furthermore, the legal status of cryptocurrencies, which are often integral to blockchain technology, remains unclear in many jurisdictions. Cryptocurrencies such as Bitcoin and Ethereum are used as a medium of exchange within blockchain networks, but their legal classification varies across countries. Some countries have embraced cryptocurrencies and enacted specific regulations, while others have banned or imposed restrictions on their use. This regulatory fragmentation creates uncertainty for businesses and individuals who engage in cryptocurrency transactions using blockchain technology.
Overall, the uncertainty in the legal status of blockchain technology limits its adoption and inhibits the growth of innovative applications. Clear and harmonized regulations are needed to address the legal challenges posed by blockchain technology, providing businesses and individuals with the confidence to fully embrace its potential.
Compliance Challenges
The blockchain technology has gained popularity due to its decentralized nature and ability to facilitate secure and transparent transactions. However, it is not without its limitations, especially when it comes to compliance with various regulations and standards.
One of the main compliance challenges of blockchain technology is the lack of standardization. Different countries and industries have their own sets of regulations, making it difficult for blockchain networks to comply with all of them. This can pose a problem for businesses operating on a global scale, as they need to ensure that their blockchain operations meet the legal requirements of each jurisdiction.
Another compliance challenge is privacy and data protection. While blockchain offers transparency by recording all transactions on a public ledger, it also poses a potential risk to privacy. Certain regulations, such as the European Union’s General Data Protection Regulation (GDPR), require businesses to protect personal data and ensure the right to be forgotten. However, the immutable nature of blockchain makes it difficult to delete or modify information, raising concerns about compliance with these regulations.
Additionally, the use of blockchain technology for financial transactions poses challenges in terms of anti-money laundering (AML) and know your customer (KYC) regulations. These regulations require financial institutions to verify the identity of their customers and monitor transactions for suspicious activities. Blockchain’s pseudonymous nature can make it difficult to comply with these regulations, as it may be challenging to identify the parties involved in a transaction.
Moreover, the scalability of blockchain technology is another compliance challenge. As the number of transactions and participants on a blockchain network increases, so does the size of the ledger. This can make it difficult to meet regulatory requirements related to data storage and retention periods, especially in industries with strict compliance regulations.
In conclusion, while blockchain technology offers many benefits, it also presents various compliance challenges. These include the lack of standardization, privacy concerns, difficulties in complying with AML and KYC regulations, and scalability issues. Overcoming these challenges is crucial for the widespread adoption of blockchain technology in regulated industries.
Privacy Concerns
Blockchain technology is often touted as a secure and transparent way to conduct transactions. However, it also raises several privacy concerns that need to be addressed.
First and foremost, blockchain is a decentralized ledger that records all transactions made in a particular network. While this provides transparency and immutability, it also means that anyone who has access to the network can see all the transaction details. This lack of privacy can be a major concern for individuals who do not want their financial or personal information to be widely accessible.
Another privacy concern in blockchain is the linkability of transactions. Because all transactions are recorded on the public ledger, it is possible to link different transactions together and create a profile of a user’s activities. This can potentially reveal sensitive information about an individual’s spending habits, financial situation, and even their identity.
Furthermore, smart contracts on the blockchain can also raise privacy concerns. Smart contracts are self-executing contracts with the terms of the agreement directly written into code. While they provide transparency and eliminate the need for intermediaries, they also make the terms of the contract publicly accessible. This lack of privacy can be problematic for businesses or individuals who want to keep their contractual agreements confidential.
Lastly, blockchain technology may face challenges in complying with existing data protection regulations, such as the General Data Protection Regulation (GDPR). The GDPR requires organizations to protect the personal data of individuals and provide them with certain rights, such as the right to be forgotten. However, the decentralized nature of blockchain makes it difficult to delete or modify data once it is recorded on the ledger.
In conclusion, while blockchain technology offers many benefits, it also raises privacy concerns that need to be addressed. Finding the right balance between transparency and privacy will be crucial for its wide adoption in various industries.
FAQ:
What are the key weaknesses and limitations of blockchain technology?
Blockchain technology has a few key weaknesses and limitations. One of the main limitations is scalability. As the number of users and transactions on the blockchain network increases, the network can become slower and less efficient. Additionally, the immutability of blockchain can be both a strength and a weakness. Once a transaction is recorded on the blockchain, it cannot be easily changed or reversed, which can be problematic if there are errors or fraudulent activities. Another weakness is the high energy consumption required for mining and maintaining the blockchain, leading to environmental concerns. Finally, blockchain technology also faces regulatory and legal challenges, as it operates across borders and may not align with existing regulations.
Why is scalability a weakness of blockchain technology?
Scalability is a weakness of blockchain technology because as the number of users and transactions on the network increases, the blockchain can become slow and less efficient. This is because every transaction needs to be validated and added to the blockchain by multiple nodes in the network. With a large number of transactions, this process can take a significant amount of time and resources, causing delays and congestion on the network.
What are the environmental concerns related to blockchain technology?
One of the key weaknesses of blockchain technology is its high energy consumption. Blockchain networks often rely on a consensus mechanism called proof-of-work, which requires miners to solve complex mathematical problems in order to validate transactions. This mining process requires a significant amount of computational power and energy. As a result, the energy consumption of blockchain networks can be substantial, leading to concerns about its environmental impact and carbon footprint.
How does the immutability of blockchain technology act as a weakness?
The immutability of blockchain technology, while a strength in terms of security and trustworthiness, can also act as a weakness. Once a transaction is recorded on the blockchain, it cannot be easily changed or reversed. This can be problematic if there are errors or fraudulent activities. If a mistake is made or if a transaction needs to be reversed, it requires a complex and sometimes contentious process to make changes to the blockchain. This lack of flexibility can pose challenges in certain situations where reversibility or editability is necessary.

