The global information network has come a long way since its inception, with constant advancements in technology revolutionizing the way we exchange information. One such groundbreaking development is the Galileo Accelerated Library (GAL), a futuristic platform that promises to redefine the way we access and disseminate information.
GAL combines the power of artificial intelligence (AI) with the vast repository of human knowledge to create an unparalleled resource for information seekers. With its cutting-edge algorithms, GAL is capable of processing, organizing, and analyzing data at an unprecedented speed, making it the ultimate tool for researchers, students, and professionals alike.
What sets GAL apart from other information exchange platforms is its ability to adapt and evolve. As users interact with GAL, the AI algorithms learn from their behaviors and preferences, constantly refining and personalizing the user experience. This means that with each search, GAL becomes better at understanding individual needs and providing tailored recommendations, ensuring that users are always one step ahead in their quest for knowledge.
Understanding GAL

GAL (Global Access Layer) is a revolutionary technology that aims to redefine the way information is exchanged and stored. It provides a decentralized and secure platform for individuals, businesses, and organizations to share and access data without the need for intermediaries.
GAL leverages blockchain technology to ensure transparency, immutability, and tamper-proof data records. By utilizing distributed ledger technology, GAL eliminates the need for a centralized authority, reducing the risk of data breaches and providing users with more control over their information.
One of the key advantages of GAL is its ability to facilitate seamless cross-platform and cross-application data sharing. With GAL, users can securely share data across different systems, applications, and devices, enabling better collaboration and integration between various parties.
GAL also offers data privacy and security features, allowing users to selectively share their information with specific individuals or groups. This granular control ensures that data is only accessible to authorized parties, protecting sensitive information from unauthorized access.
To learn more about how GAL works and how to make Galxe (GAL), visit the official website: How to make Galxe (GAL).
| Key Features of GAL: |
|---|
| Decentralized data exchange |
| Transparency and immutability |
| Secure cross-platform data sharing |
| Granular data privacy controls |
GAL Benefits

Global Accessible Language (GAL) offers numerous benefits for individuals and organizations seeking to exchange information in a globalized world. These benefits include:
- Increased Accessibility: GAL allows for seamless communication and information exchange across different languages and cultures. It breaks down language barriers and enables individuals and businesses to easily access information in their preferred language, making it more inclusive and accessible for everyone.
- Improved Efficiency: With GAL, organizations can streamline their processes and reduce the time and effort required to translate and localize content. By utilizing GAL, businesses can access multilingual content instantly, making communication faster and more efficient.
- Cost Savings: GAL eliminates the need for multiple translation services or language experts, resulting in cost savings for organizations. By leveraging GAL, businesses can reduce translation expenses and allocate resources more effectively.
- Enhanced Collaboration: GAL promotes collaboration among individuals from different linguistic backgrounds. It allows teams to work together seamlessly, regardless of their native language, facilitating knowledge sharing and improving productivity.
- Cultural Understanding: GAL helps bridge cultural gaps by enabling individuals to communicate and share information in a way that is culturally sensitive and appropriate. It encourages understanding and appreciation of different cultures, fostering global connections and cooperation.
Overall, GAL offers a range of significant benefits, from increased accessibility and efficiency to cost savings and enhanced collaboration. Embracing GAL can help individuals and organizations thrive in an interconnected world, where effective information exchange is crucial for success.
Improved Communication and Collaboration
The future of information exchange holds great promise for improved communication and collaboration. With the advancement of technology, it is becoming easier than ever to connect and share ideas with others.
One of the ways in which communication and collaboration are being enhanced is through the development of more efficient and intuitive messaging platforms. These platforms allow individuals and teams to communicate in real-time, no matter where they are located. Features such as instant messaging, video conferencing, and file sharing help to streamline communication and make collaboration more effective.
Additionally, the use of artificial intelligence (AI) in communication tools is revolutionizing the way we interact with information. AI-powered chatbots can provide instant responses to inquiries, freeing up time for more meaningful conversations. Machine learning algorithms can also analyze data and provide valuable insights, enabling teams to make more informed decisions.
Furthermore, the rise of cloud computing has greatly facilitated communication and collaboration. Cloud-based platforms allow users to access and share information from anywhere, at any time. This promotes seamless collaboration, as team members can work on projects simultaneously and have real-time access to the latest updates and documents.
Collaboration tools such as project management software and virtual whiteboards also facilitate effective teamwork. These tools enable team members to work together on tasks, assign responsibilities, and track progress. With these features, communication and collaboration become more efficient, leading to improved productivity and better outcomes.
In conclusion, the future of information exchange promises many advancements in communication and collaboration. From enhanced messaging platforms to AI-powered tools, technology is revolutionizing the way we connect and share ideas. By embracing these advancements, businesses and individuals can improve their communication and collaboration capabilities, leading to greater success in the fast-paced digital world.
Enhanced Connectivity

Enhanced connectivity is at the core of GAL’s vision for the future of information exchange. With advancements in technology and the Internet of Things, we are constantly finding new ways to connect and communicate with one another.
One key aspect of enhanced connectivity is the ability to seamlessly connect devices and systems together. Through the development of standardized protocols and interfaces, GAL aims to create a network of interconnected devices that can share and exchange information in real-time.
Another crucial aspect is the improvement of internet connectivity. GAL is investing in next-generation networks and infrastructure to provide faster and more reliable internet access to users around the globe. This will enable individuals and businesses to connect and collaborate more efficiently, regardless of their location.
In addition to physical connectivity, GAL is also focused on enhancing virtual connectivity. We are developing advanced communication tools and platforms that enable users to connect and interact with one another in immersive and meaningful ways. These technologies, such as augmented reality and virtual reality, have the potential to revolutionize how we communicate and collaborate in the digital age.
In conclusion, enhanced connectivity is essential for the future of information exchange. GAL is committed to pushing the boundaries of connectivity through technological advancements, improved internet access, and innovative communication tools. By embracing enhanced connectivity, we can create a more connected and collaborative world.
Streamlined Workflow

One of the most significant advantages of GAL’s Future of Information Exchange is its ability to streamline workflows. With GAL, organizations can improve efficiency, productivity, and collaboration by automating manual tasks and simplifying processes.
By leveraging GAL’s advanced technologies, such as artificial intelligence and machine learning, organizations can automate repetitive and time-consuming tasks. This not only frees up employees’ time but also reduces the risk of human error. For example, GAL can automatically organize and categorize incoming emails, saving employees from having to sort through their inbox manually.
GAL also offers seamless integration with existing systems and tools, allowing organizations to centralize their information exchange. Whether it’s sharing documents, collaborating on projects, or communicating with team members, GAL provides a unified platform that brings everything together in one place. This eliminates the need for employees to switch between multiple applications or platforms, saving time and effort.
Furthermore, GAL’s Future of Information Exchange includes robust security features to protect sensitive data. With GAL, organizations can ensure that information is encrypted, securely stored, and only accessible to authorized personnel. This not only safeguards confidential information but also ensures compliance with data protection regulations.
Overall, GAL’s Future of Information Exchange offers a streamlined workflow that enhances efficiency, productivity, and security. By automating tasks, consolidating tools, and implementing robust security measures, organizations can optimize their operations and stay ahead in the information-driven world.
Real-time Updates

In today’s fast-paced world, staying updated with the latest information is crucial. Traditional information exchange methods like emails and newsletters might not always provide timely updates. That’s where real-time updates come in.
Real-time updates allow users to receive information instantly as it happens. Whether it’s news, stock prices, or social media updates, real-time updates enable users to stay in the loop and make timely decisions.
With the advancement in technology, real-time updates have become more accessible. Internet connectivity has improved, and smartphones and wearable devices have made it easier than ever to receive real-time updates on the go.
Real-time updates have revolutionized various industries. For example, in the financial sector, traders can now receive real-time updates on market conditions, helping them make informed investment decisions. In the healthcare industry, real-time updates enable doctors and healthcare professionals to monitor patients’ vital signs and respond quickly in case of emergencies.
Real-time updates also have benefits in the world of social media. Platforms like Twitter and Facebook utilize real-time updates to keep users updated with the latest posts, news, and events. This has changed the way people consume information and stay connected with others.
Furthermore, real-time updates have been instrumental in emergency situations. During natural disasters or crisis situations, real-time updates help authorities and individuals stay informed about evacuation orders, safety guidelines, and other critical information.
However, with real-time updates, there are also challenges. The sheer volume of information can be overwhelming, and users need to filter out irrelevant updates to focus on what matters. Additionally, ensuring the accuracy and reliability of real-time updates is crucial, as false or misleading information can spread rapidly.
In conclusion, real-time updates have greatly transformed how we exchange information. With the ability to receive instantaneous updates, users can stay informed, make better decisions, and respond quickly to changing situations. As technology continues to advance, real-time updates will play an even more significant role in our daily lives.
Secure Data Sharing
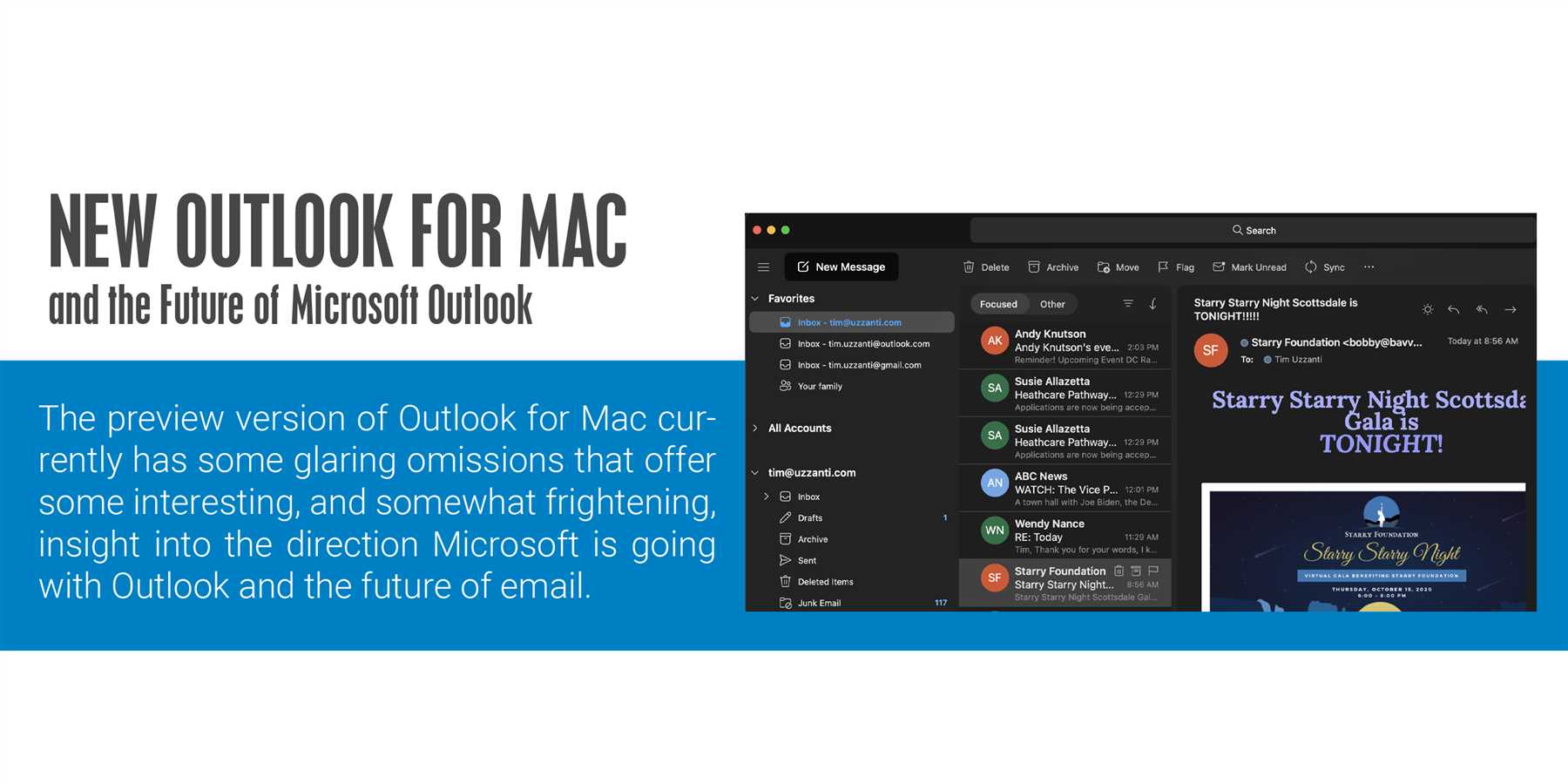
In the digital age, the exchange of information has become an integral part of our daily lives. However, with the increase in connectivity, there is a growing concern about the security of our data. It is essential to ensure that sensitive information remains protected during the process of data sharing.
Secure data sharing refers to the practice of exchanging information while maintaining confidentiality, integrity, and availability. There are various methods and technologies available to achieve secure data sharing.
One such method is encryption, which involves encoding data using cryptographic algorithms to make it unreadable to unauthorized individuals. Encryption is widely used to protect data in transit as well as at rest. By encrypting data before it is shared, organizations can ensure that only authorized recipients can access and decrypt the information.
Another technique for secure data sharing is access control. This involves implementing measures such as authentication and authorization to control who can access and modify the data. Access control helps prevent unauthorized individuals from gaining access to sensitive information, reducing the risk of data breaches.
In addition to encryption and access control, secure data sharing can also be achieved through the use of secure communication protocols, such as HTTPS or SFTP. These protocols provide an added layer of security by encrypting data during transmission and verifying the authenticity of the sender and receiver.
Furthermore, practices such as data anonymization and data minimization can enhance the security of data sharing. Data anonymization involves removing personally identifiable information from datasets, reducing the risk of re-identification and protecting individual privacy. Data minimization, on the other hand, involves only sharing the necessary minimum amount of data required for a specific purpose, thereby reducing the potential impact of a data breach.
Overall, secure data sharing is crucial in ensuring the privacy and security of sensitive information. By employing encryption, access control, secure communication protocols, and other best practices, organizations can mitigate the risk of unauthorized access, data breaches, and other security incidents. It is essential for individuals and organizations to stay vigilant and adopt robust security measures to protect their data in an increasingly interconnected world.
End-to-end Encryption

As the exchange of information becomes increasingly digital, the need for secure communication has grown. End-to-end encryption is a method of protecting data as it is transmitted from one device to another by encrypting it at the source and decrypting it at the destination.
With end-to-end encryption, only the sender and the intended recipient have the encryption keys necessary to access the encrypted data. This means that even if the data is intercepted during transit, it is nearly impossible for anyone else to read or modify it.
End-to-end encryption provides a high level of security and privacy for users. It ensures that sensitive information, such as financial transactions or personal messages, remains confidential. This is especially important in today’s digital landscape, where cyber threats are constantly evolving.
There are various methods and algorithms used for implementing end-to-end encryption. One common technique is public key cryptography, where each user has a public key for encryption and a private key for decryption. Another approach is symmetric key encryption, where both the sender and receiver share a secret key.
While end-to-end encryption provides strong security for individual users, it also presents challenges for law enforcement and governmental agencies. Because the data is encrypted, it can be difficult to access and monitor communications in cases of criminal investigations or national security concerns.
Overall, end-to-end encryption offers a crucial layer of protection in the modern information age. It allows users to communicate and share data securely, ensuring that their privacy and sensitive information remain intact.
Access Control

Access control plays a critical role in ensuring the security and privacy of information exchange. It involves defining and enforcing the rules and policies that determine who can access certain information and what actions they can perform with it. By setting up access controls, organizations can limit the exposure of sensitive data to unauthorized individuals or entities.
Access control mechanisms can be divided into three main categories: identification, authentication, and authorization. Identification is the process of recognizing and collecting information about individuals, such as usernames or employee IDs. Authentication is the verification process that ensures the claimed identity matches the provided credentials. Authorization determines what resources or actions an authenticated user is allowed to access based on their assigned permissions.
Access control systems can range from simple username and password combinations to advanced biometric authentication methods like fingerprint or face recognition. Additionally, organizations can implement role-based access control (RBAC), where permissions are assigned based on job roles or hierarchical levels within the organization.
Effective access control is essential in preventing unauthorized access, data breaches, or misuse of information. It helps organizations maintain confidentiality, integrity, and availability of their critical data. By implementing robust access control measures, organizations can confidently exchange information knowing that it is only accessible to authorized individuals.
Auditing and Compliance

In the future of information exchange, auditing and compliance will play a crucial role in ensuring the integrity and security of data. As more and more information is being shared and accessed through various channels, it becomes essential to have robust auditing mechanisms to track and monitor the flow of data.
Auditing involves the systematic examination and evaluation of data to ensure compliance with established standards and regulations. It helps identify any discrepancies, anomalies, or violations in the information exchange process. By keeping a detailed record of all data transactions, auditing provides a valuable tool for forensic analysis and investigation.
Compliance refers to adhering to laws, regulations, and industry standards governing the sharing and protection of sensitive information. It encompasses data privacy, security, and confidentiality. Organizations need to establish comprehensive compliance programs that include policies, procedures, and protocols to safeguard data and minimize risks.
Effective auditing and compliance mechanisms help organizations maintain trust and credibility with their stakeholders. They demonstrate a commitment to data protection, transparency, and responsible information exchange. Regular audits allow organizations to identify and address vulnerabilities in their systems promptly.
In conclusion, as the future of information exchange evolves, businesses and organizations must prioritize auditing and compliance. By implementing robust auditing mechanisms and ensuring compliance with relevant regulations, they can uphold the confidentiality and integrity of data, protect against cybersecurity threats, and maintain the trust of their customers.
FAQ:
What is GAL?
GAL stands for Global Accessible Language. It is an advanced technology that allows seamless and efficient exchange of information between different languages and cultures.
How does GAL work?
GAL works by combining artificial intelligence, natural language processing, and machine learning algorithms to analyze and understand the context and nuances of different languages. It then translates and adapts the information for efficient communication and understanding.
What are the benefits of GAL?
GAL provides numerous benefits such as enhanced global communication, improved cross-cultural collaboration, increased accessibility to information, and reduced language barriers. It can revolutionize the way we exchange and understand information in a diverse world.
Can GAL be used in different industries?
Yes, GAL can be utilized in various industries such as international business, tourism, education, healthcare, and more. It has the potential to streamline communication and facilitate global interactions in any field where language barriers exist.
What are the future implications of GAL?
The future implications of GAL are vast. It can contribute to the development of a more inclusive and connected world, foster cultural understanding, and pave the way for new opportunities in global trade, education, and diplomacy. Ultimately, GAL has the potential to reshape the way we communicate and collaborate on a global scale.

