As technology continues to advance at an exponential rate, the need for secure and efficient login systems has become increasingly important. With cybercrime on the rise and user data more vulnerable than ever, businesses and individuals alike are searching for solutions that offer maximum protection without sacrificing user experience. Enter Login Galxe (GAL) – a cutting-edge login system that combines state-of-the-art security measures with seamless user interface.
What sets Login Galxe (GAL) apart from traditional login systems is its multifactor authentication process, which adds an extra layer of security to protect against unauthorized access. By requiring users to authenticate their identity through a combination of something they know (such as a password), something they have (such as a mobile device), and something they are (such as a fingerprint or facial recognition), Login Galxe (GAL) ensures that only authorized individuals can access sensitive information.
In addition to its robust security features, Login Galxe (GAL) is designed for maximum efficiency. By incorporating advanced algorithms and machine learning capabilities, the system is able to identify patterns and detect anomalies in user behavior, allowing for real-time threat detection. This not only minimizes the risk of unauthorized access, but also enables businesses to proactively address potential security breaches before they can cause any harm.
Furthermore, Login Galxe (GAL) offers a seamless user experience that is both intuitive and user-friendly. With a clean and minimalistic design, the login interface is easy to navigate and understand, eliminating user frustration and reducing the likelihood of password-related issues. Whether accessing their accounts from a desktop, tablet, or mobile device, users can enjoy a hassle-free login experience that enhances both security and efficiency.
In conclusion, Login Galxe (GAL) is the ultimate solution for optimizing security and efficiency in login systems. By combining state-of-the-art security measures, multifactor authentication, real-time threat detection, and a user-friendly interface, Login Galxe (GAL) provides businesses and individuals with peace of mind and a streamlined login experience. Upgrade your login system today and take your security to the next level with Login Galxe (GAL).
Enhance Your Security Measures
Enhancing security measures is crucial in today’s rapidly evolving digital landscape. With the Login Galxe (GAL) platform, you can optimize your security protocols and protect your sensitive data from unauthorized access.
Here are a few ways GAL can enhance your security measures:
- Two-Factor Authentication (2FA): GAL offers a robust 2FA system that adds an extra layer of security to your login process. By requiring users to provide a second form of verification, such as a unique code generated by a mobile app, GAL prevents unauthorized access even if login credentials are compromised.
- Advanced Encryption: GAL utilizes advanced encryption algorithms to protect your data during transmission and storage. This ensures that even if intercepted, your information remains unreadable and secure.
- Secure Password Policies: GAL allows you to enforce strong password policies, including requirements for passwords to have a minimum length, a mixture of uppercase and lowercase letters, numbers, and special characters. By implementing and enforcing these policies, GAL helps prevent weak passwords and improves overall security.
- Session Management: GAL offers comprehensive session management features, such as session timeouts and token-based authentication. This helps prevent unauthorized access to user accounts and protects against session hijacking attacks.
- Logging and Monitoring: GAL provides logs and monitoring capabilities to track user activities and detect any suspicious behavior. By closely monitoring user access and activity, GAL helps identify potential security threats and allows for timely action to be taken.
With GAL, you can enhance your security measures and have peace of mind knowing that your data is protected against unauthorized access and potential security breaches. Invest in GAL today and take your security to the next level.
“`html
Streamline User Authentication
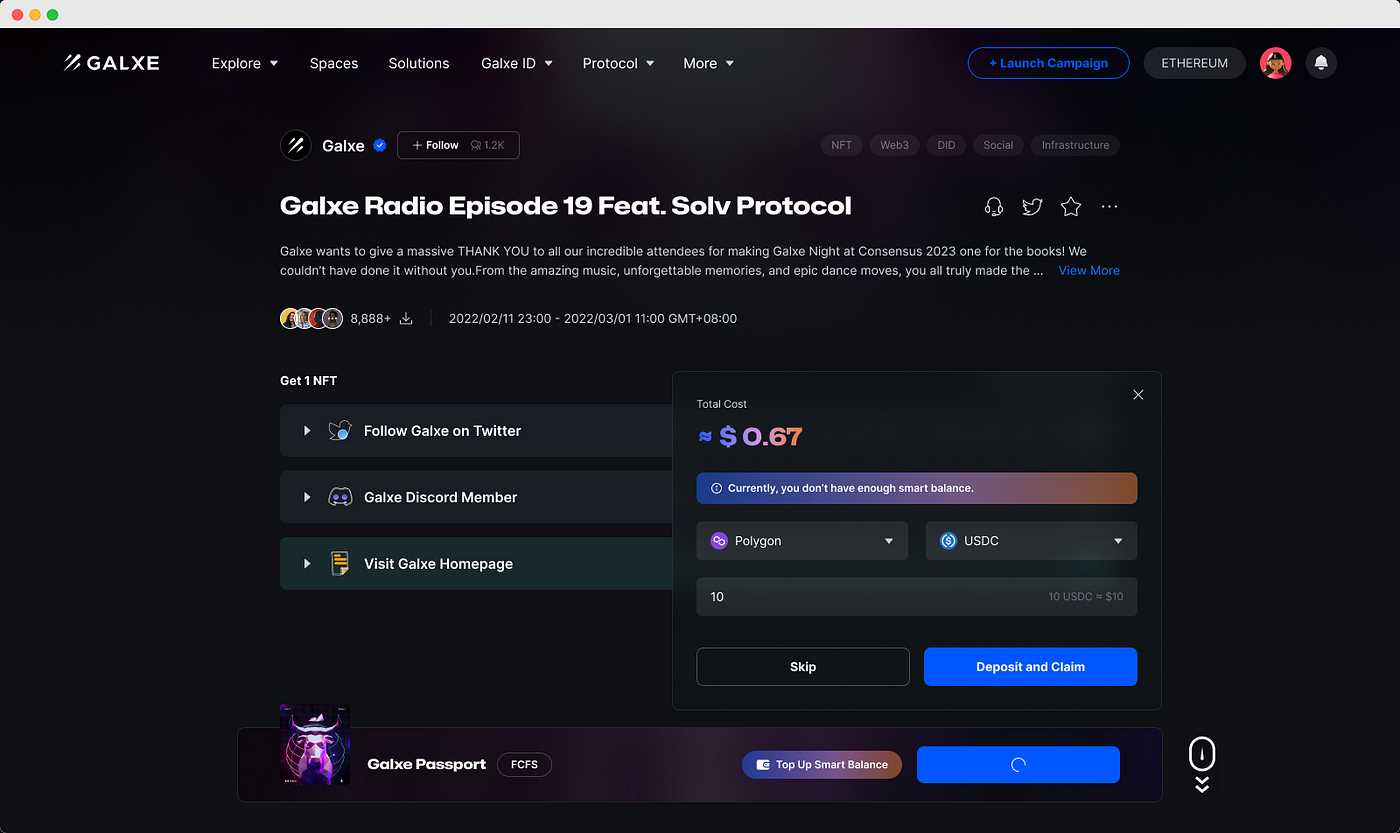
The login process is a critical component of any application’s security. It serves as the gateway for users to access their accounts and ensures that only authorized individuals can access sensitive information. However, traditional login methods can be cumbersome and time-consuming for both users and administrators.
With the introduction of Galxe (GAL), a new era of user authentication has begun. GAL provides a streamlined login experience that combines security and efficiency, making it the ideal solution for modern applications.
By leveraging decentralized technology, Galxe simplifies the user authentication process. Instead of relying on complex passwords and username combinations, GAL uses advanced encryption algorithms to create unique identifiers for each user. These identifiers are securely stored on the blockchain, making them virtually impossible to hack or manipulate.
Streamlining user authentication is not only beneficial for users but also for administrators. With GAL, administrators can easily manage user accounts, set up role-based access controls, and monitor authentication activities in real-time. This centralized control enhances security while reducing administrative overhead.
Moreover, GAL’s efficient authentication process minimizes the risk of human error that can result in security breaches. With features like two-factor authentication and biometric recognition, GAL ensures that only authorized individuals can gain access to user accounts.
In conclusion, Galxe (GAL) revolutionizes the way user authentication is done. By streamlining the login process and enhancing security measures, GAL offers a secure and efficient solution for modern applications. To learn more about GAL and its benefits, visit price today Galxe (GAL).
Key Features of Login Galxe
Login Galxe offers a range of key features that optimize security and efficiency for users. These features include:
- Secure Authentication: Login Galxe uses advanced encryption algorithms to ensure secure authentication. This protects user credentials from unauthorized access and keeps sensitive information safe.
- Multi-Factor Authentication: With Login Galxe, you can enable multi-factor authentication for an added layer of security. Users are required to provide additional authentication factors, such as a fingerprint or a one-time password, to verify their identity.
- Seamless Integration: Login Galxe seamlessly integrates with existing systems and applications. It supports a wide range of authentication protocols, making it easy to implement in various environments.
- Password Management: Login Galxe provides efficient password management capabilities. Users can securely store and manage their passwords, eliminating the need to remember multiple complex passwords.
- Single Sign-On (SSO): With Login Galxe’s SSO functionality, users only need to authenticate once to gain access to multiple applications. This streamlines the login process and improves user productivity.
- Flexible Access Control: Login Galxe allows administrators to define and enforce access control policies. This enables the granting or revocation of user access to specific resources or applications based on predefined rules.
- Activity Monitoring: Login Galxe tracks user activity and generates detailed logs. This helps administrators identify potential security threats or breaches and take appropriate actions.
- Reporting and Auditing: Login Galxe offers reporting and auditing capabilities, allowing administrators to generate comprehensive reports on user access, authentication attempts, and system usage. This helps in meeting regulatory compliance requirements.
By leveraging these key features, Login Galxe helps organizations enhance security, streamline authentication processes, and improve overall efficiency.
Advanced Encryption Technology
One of the key components of Login Galxe’s security solution is its advanced encryption technology. Encryption plays a vital role in protecting sensitive information from unauthorized access, ensuring the confidentiality and integrity of data during transmission and storage.
Login Galxe utilizes state-of-the-art encryption algorithms to secure user login credentials and other sensitive data. These algorithms use complex mathematical operations to convert plain text into an unreadable format, commonly known as ciphertext. Only authorized parties with the correct decryption keys can access and decipher the ciphertext, transforming it back into its original form.
The encryption technology used by Login Galxe is based on industry-standard cryptographic algorithms, including AES (Advanced Encryption Standard), RSA (Rivest-Shamir-Adleman), and SHA (Secure Hash Algorithm). These encryption algorithms have undergone extensive analysis and have been recognized for their robustness and security.
In addition to using strong encryption algorithms, Login Galxe also implements secure key management practices. The encryption keys used to encrypt and decrypt data are securely stored and managed, reducing the risk of key compromise or unauthorized access.
With Login Galxe’s advanced encryption technology, businesses and organizations can have peace of mind knowing that their data is protected against unauthorized access and potential cyber threats. By encrypting sensitive information, Login Galxe helps ensure that even if a data breach occurs, the stolen data remains unintelligible and useless to attackers.
Overall, the advanced encryption technology employed by Login Galxe is a crucial aspect of its security solution, providing a strong defense against potential security breaches and enhancing the overall efficiency and reliability of the login process.
Two-Factor Authentication
Two-Factor Authentication (2FA) is an added layer of security that requires users to provide two forms of identification before gaining access to a system or account. This method provides an extra level of protection compared to traditional username and password authentication.
With 2FA, users are typically required to enter their username and password as the first factor. The second factor can vary depending on the implementation, but commonly includes something the user knows (such as a unique pin or answer to a security question) or something the user has (such as a physical token or mobile app). The combination of these two factors significantly reduces the risk of unauthorized access, as an attacker would need to possess both factors to successfully breach the system or account.
One common implementation of 2FA is the use of One-Time Passwords (OTP). These are temporary codes that are typically sent to the user’s mobile device and must be entered in addition to the username and password. OTPs provide an additional layer of security as they are only valid for a short period of time and can only be used once.
Another popular method of 2FA is biometric authentication, which uses unique physical characteristics of the user, such as fingerprints or facial recognition, as the second factor. This method provides a high level of security as biometric data is difficult to replicate or forge.
Implementing 2FA can significantly strengthen the security of a system or account, as it requires an attacker to possess multiple forms of identification. It is important, however, to ensure that the second factor is not easily guessable or vulnerable to interception. Additionally, users should be educated on the importance of maintaining the security of their second factor (such as not sharing OTPs or physical tokens).
Overall, Two-Factor Authentication is a powerful tool in the fight against unauthorized access. By requiring users to provide two forms of identification, systems and accounts can be better protected, and the risk of data breaches and other security incidents can be significantly reduced.
Single Sign-On Integration

Integrating GAL into your existing single sign-on (SSO) infrastructure can significantly enhance security and efficiency for your organization. GAL supports popular SSO protocols, such as SAML and OAuth, allowing seamless integration with your current authentication system.
With GAL’s SSO integration, users can log in to multiple applications and systems with just one set of credentials. This eliminates the need for users to remember and manage multiple usernames and passwords, reducing the risk of weak or compromised passwords.
In addition to improving security, GAL’s SSO integration also enhances efficiency by streamlining the login process. Users no longer need to spend time entering their credentials for each individual application or system. This saves time and increases productivity, particularly for organizations with a large number of applications or systems that require authentication.
GAL’s SSO integration also provides centralized control over user access and permissions. Administrators can easily manage user access to different applications and systems from a single interface, making it easier to grant or revoke access as needed. This helps enforce security policies and ensures that only authorized users can access sensitive resources.
Overall, GAL’s SSO integration offers a comprehensive solution for optimizing security and efficiency within your organization. By integrating GAL with your existing SSO infrastructure, you can simplify the login process, enhance security, and improve productivity for your users.
Benefits of Implementing Login Galxe
Implementing Login Galxe provides several benefits for both security and efficiency. Here are some of the key advantages:
Enhanced security: Login Galxe offers advanced security measures to protect your online accounts. It utilizes robust authentication methods, including two-factor authentication, biometric authentication, and hardware tokens. These techniques help prevent unauthorized access and protect sensitive data from potential threats.
Streamlined user experience: Login Galxe aims to provide a seamless and user-friendly login process. It offers a single sign-on (SSO) feature, allowing users to access multiple applications and services with just one set of login credentials. This eliminates the need for remembering different usernames and passwords, simplifying the user experience.
Improved efficiency: By implementing Login Galxe, organizations can streamline their login process, saving time and improving overall efficiency. Users can quickly authenticate themselves and gain access to the desired resources without the need for complex and time-consuming traditional login methods.
Reduced risk of password-related issues: Password-related issues, such as forgotten passwords or weak passwords, can be a significant concern for organizations. Login Galxe addresses these issues by offering password recovery options, password strength requirements, and password management tools. This reduces the risk of password-related security breaches and minimizes potential impacts on productivity.
Centralized access control: Login Galxe allows organizations to have centralized control over user access to different resources. Administrators can easily manage user permissions, granting or revoking access as necessary, ensuring that only authorized individuals can access specific applications or data.
Audit trail and reporting: Login Galxe provides a comprehensive audit trail and reporting system, allowing administrators to monitor and track user activities. This can be helpful in identifying potential security risks, investigating security incidents, and ensuring compliance with regulatory requirements.
Overall, implementing Login Galxe can significantly enhance security, simplify the user experience, and improve efficiency for organizations and individuals alike.
Improved Protection against Cyber Threats
In today’s digital world, protecting sensitive information from cyber threats has become a top priority for organizations. With the increasing sophistication of hackers and cybercriminals, traditional security measures are no longer enough to safeguard valuable data.
Login Galxe (GAL) takes security to the next level by offering improved protection against cyber threats. GAL utilizes advanced encryption algorithms to ensure that login credentials are securely stored and transmitted. This prevents unauthorized access and mitigates the risk of data breaches.
One of the key features of GAL is its multi-factor authentication (MFA) capability. MFA adds an extra layer of security by requiring users to authenticate themselves through multiple means, such as a password and a biometric identifier. This significantly reduces the risk of unauthorized access, as even if one factor is compromised, the others provide an additional level of protection.
GAL also offers real-time threat monitoring and analysis. It continuously analyzes login patterns and behavior to detect any irregularities or suspicious activity. If any suspicious activity is detected, GAL immediately alerts the system administrators, enabling them to take swift action to mitigate the potential threat.
Furthermore, GAL incorporates machine learning algorithms to constantly learn and adapt to new cyber threats. This ensures that the system is always up-to-date with the latest security protocols and measures, providing a proactive defense against emerging threats.
With GAL, organizations can have peace of mind knowing that their valuable data is protected against cyber threats. The improved security features offered by GAL help reduce the risk of unauthorized access, data breaches, and other cyberattacks. By implementing GAL, organizations can optimize their security and efficiency, enabling them to focus on their core business operations without worrying about cybersecurity.
Protect your organization’s sensitive information with Login Galxe (GAL) and gain a competitive edge in today’s digital landscape.
Reduced Risk of Unauthorized Access
One of the main concerns for any organization is the risk of unauthorized access to its systems and sensitive information. Login Galxe (GAL) is designed to address this concern by implementing various security measures.
Firstly, GAL uses multi-factor authentication, which requires users to provide more than one form of identification to access their accounts. This significantly reduces the risk of unauthorized access, as even if one factor is compromised, the attacker would still need to bypass additional layers of security.
Secondly, GAL implements strong password policies, ensuring that users create and manage strong, unique passwords. This prevents attackers from easily guessing or brute-forcing passwords to gain unauthorized access.
Furthermore, GAL offers features like session timeouts and idle locks, which automatically log out users after a period of inactivity. This minimizes the risk of unauthorized access in case a user forgets to log out or leaves their device unattended.
In addition to these measures, GAL implements robust encryption algorithms to protect user data during transit and storage. This ensures that even if an attacker somehow intercepts the data, they won’t be able to read or use it without the encryption key.
Lastly, GAL provides detailed audit logs and real-time monitoring capabilities, allowing organizations to track and identify suspicious activities. This helps in quickly detecting and mitigating potential security breaches before they can cause any harm.
In conclusion, GAL significantly reduces the risk of unauthorized access by implementing multi-factor authentication, strong password policies, session management features, encryption algorithms, and advanced monitoring capabilities. By utilizing GAL, organizations can enhance their security posture and protect sensitive information from unauthorized access.
Efficient User Management
Efficient user management is a crucial aspect of any secure and optimized system. Login Galxe (GAL) provides a comprehensive solution for managing user accounts effectively.
With GAL, administrators can easily create, update, and delete user accounts, granting or revoking access privileges as needed. The system allows for efficient user onboarding and offboarding processes, minimizing the time and effort required by administrators.
GAL also offers features to streamline user authentication and authorization. It supports various authentication methods, including password-based authentication, two-factor authentication, and social media account integration. This flexibility allows organizations to choose the authentication methods that best suit their security requirements and user preferences.
Furthermore, GAL provides robust user role and permission management capabilities. Administrators can assign specific roles to users, granting them access to only the necessary features and functionalities. This granular control over user permissions ensures that sensitive information and critical system resources are protected from unauthorized access.
Additionally, GAL offers a user-friendly interface for users to manage their own accounts efficiently. Users can update their personal information, reset passwords, and manage their authentication preferences conveniently. This self-service functionality reduces the burden on administrators and empowers users to take control of their own accounts securely.
Overall, efficient user management is essential for maintaining a secure and streamlined system. Login Galxe (GAL) provides a comprehensive solution that simplifies user administration, enhances security, and empowers users.
Implementation Process
Implementing Login Galxe (GAL) is a straightforward process that involves the following steps:
- Assess Your Needs: Evaluate your organization’s security requirements and identify the areas where GAL can help optimize security and efficiency.
- Choose the Right Plan: Select the GAL plan that best suits your organization’s size, level of security needed, and desired features.
- Create GAL Account: Sign up for a GAL account and provide the necessary information to set up your organization’s login system.
- Configure GAL Settings: Customize the GAL settings to match your organization’s branding and security preferences.
- Add Users: Import or manually enter the user data into GAL, including their login credentials and any additional information required.
- Integrate GAL with Existing Systems: Connect GAL to your organization’s existing systems, such as databases or identity providers, to enable seamless login authentication.
- Test and Refine: Conduct thorough testing to ensure that GAL is functioning correctly and meeting your organization’s security and efficiency goals. Revise the settings or configurations as needed.
- Train Users: Provide training and support to your organization’s users to familiarize them with the GAL login process and any additional security measures.
- Go Live: Once all the necessary steps have been completed, launch GAL and start reaping the benefits of optimized security and efficiency in your login system.
By following this implementation process, your organization can seamlessly integrate GAL and enhance your overall security measures while improving the efficiency of your login system.
Integration with Existing Systems
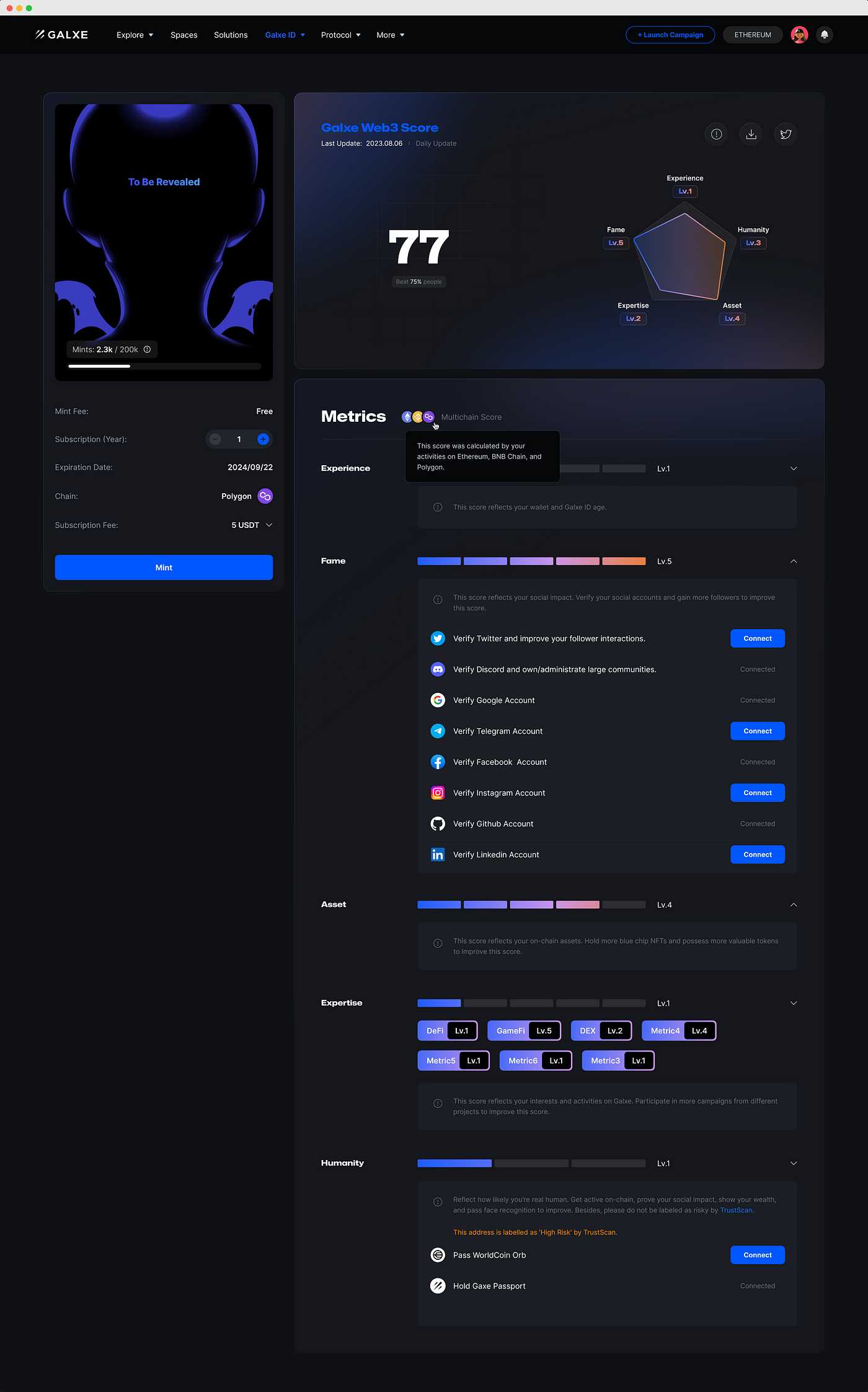
One of the key advantages of Login Galxe (GAL) is its seamless integration with existing systems. Whether you have an in-house custom-built system or use popular third-party software, GAL can easily integrate and enhance your existing security measures.
GAL provides a simple and secure way to authenticate users, granting access only to authorized individuals. By seamlessly integrating GAL with your existing login system, you can leverage the power of GAL’s advanced security features without disrupting your current workflows.
With GAL’s integration capabilities, you can enhance your system’s security by implementing multi-factor authentication, biometric authentication, or any other advanced authentication method supported by GAL. This integration ensures that only legitimate users can access your system, preventing unauthorized access and potential security breaches.
In addition to security enhancements, GAL’s integration with existing systems offers increased efficiency. By streamlining the login process and eliminating the need for users to remember multiple login credentials, GAL improves user experience and reduces the time spent on authentication.
Furthermore, GAL’s integration capabilities extend beyond login authentication. It can seamlessly integrate with your existing user management systems, allowing you to manage user accounts, roles, and permissions centrally. This integration simplifies user administration tasks and reduces the risk of errors or discrepancies in user data.
Whether you have an on-premises system or a cloud-based software, GAL’s flexible integration options ensure that you can easily incorporate GAL into your existing architecture. GAL supports industry-standard protocols and APIs, making integration with popular systems a breeze.
In conclusion, Login Galxe (GAL) offers seamless integration with existing systems, enabling enhanced security and improved efficiency. By integrating GAL with your current login and user management systems, you can leverage GAL’s advanced authentication features and streamline user administration. With GAL’s flexible and robust integration capabilities, you can optimize your system’s security while maintaining a smooth user experience.
FAQ:
What is Login Galxe (GAL)?
Login Galxe (GAL) is a security solution that helps optimize security and efficiency in login processes. It provides a secure and user-friendly way for users to authenticate themselves and access their accounts.
How does Login Galxe (GAL) optimize security?
Login Galxe (GAL) optimizes security by using advanced encryption algorithms to protect user credentials and sensitive data. It also includes features like multifactor authentication and secure session management to prevent unauthorized access to accounts.
What are the benefits of using Login Galxe (GAL)?
Using Login Galxe (GAL) offers several benefits. It improves the security of login processes, reduces the risk of unauthorized access, and minimizes the potential for data breaches. It also enhances the efficiency of logging in by providing a user-friendly and streamlined experience.
Can Login Galxe (GAL) be integrated with existing login systems?
Yes, Login Galxe (GAL) can be easily integrated with existing login systems. It provides APIs and SDKs that allow developers to integrate the solution into their applications and platforms seamlessly.
Is Login Galxe (GAL) suitable for both businesses and individuals?
Yes, Login Galxe (GAL) is suitable for both businesses and individuals. It can be implemented by organizations to enhance security in their login processes, and it can also be used by individuals who want to secure their personal accounts and information.

