Smart contracts have gained immense popularity in recent years, being heralded as the future of financial transactions and decentralized applications. These self-executing contracts not only eliminate the need for intermediaries, but also promise increased security and efficiency. However, beneath their seemingly flawless exterior, smart contracts hide a multitude of vulnerabilities that can have disastrous consequences.
One of the major vulnerabilities of smart contracts lies in their immutable nature. Once a contract is deployed on a blockchain, it cannot be modified or revoked. While this feature ensures transparency and trust, it also means that any mistakes or loopholes in the code are permanent. Inadequate testing or a single line of faulty code can lead to catastrophic outcomes, ranging from financial loss to complete system failure.
Additionally, the autonomous nature of smart contracts can sometimes be a double-edged sword. While their ability to self-execute without human intervention is a great advantage, it also means that they are susceptible to exploitation and manipulation. Hackers can identify vulnerabilities in the code and exploit them to siphon funds or disrupt the operations of decentralized applications.
Furthermore, smart contracts often rely on external data sources, called oracles, to make decisions or trigger certain actions. This dependency on external data introduces another vulnerability, as the oracles can be manipulated or provide incorrect information. This can lead to unexpected outcomes or enable attackers to trick the smart contract into executing malicious actions.
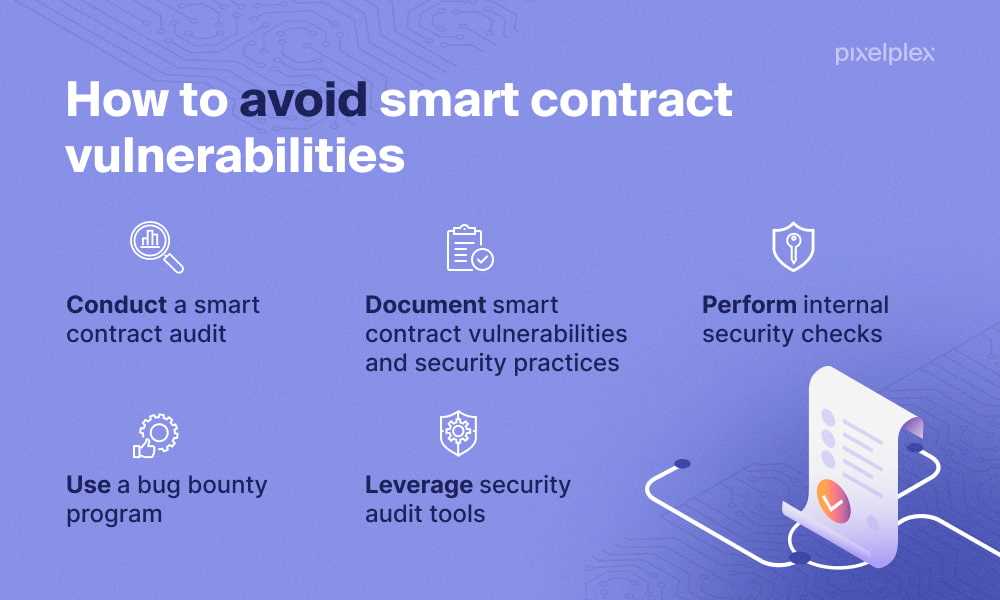
As the utilization of smart contracts continues to expand, it becomes increasingly crucial to understand and address these vulnerabilities. Thorough auditing, rigorous testing, and secure coding practices are essential steps towards mitigating the risks associated with smart contracts. By taking a closer look at the vulnerabilities and learning from past incidents, we can build a stronger foundation for the future of blockchain technology.
Understanding the Risks
When it comes to smart contracts, it is important to understand the potential risks involved. While smart contracts offer numerous benefits, they also come with their fair share of vulnerabilities. By grasping these risks, developers and users can take steps to mitigate them and ensure the security of their transactions.
One of the main risks associated with smart contracts is the possibility of programming errors. A single mistake in the code can lead to serious consequences, such as financial loss or exploitation by malicious actors. Therefore, it is crucial for developers to thoroughly audit and test their smart contracts to identify and fix any vulnerabilities before deployment.
Additionally, the decentralized nature of smart contracts introduces another layer of risk. Unlike traditional contracts that are enforced by legal authorities, smart contracts rely on code to execute transactions. If a flaw exists within the code, it can be exploited by attackers without any recourse for the affected parties. Users must be vigilant and carefully review the code and security measures implemented in the smart contract before engaging with it.
Furthermore, the immutability of smart contracts can also be a double-edged sword. While the inability to modify the code after deployment provides transparency and trust, it can pose challenges if errors are discovered or if the contract needs to be updated. The lack of a central authority to make changes means that any modifications would require consensus from all parties involved, which can be a complex and time-consuming process.
Lastly, the nascent nature of blockchain technology itself adds a level of uncertainty and risk. As the technology evolves, new vulnerabilities and attack vectors may emerge, requiring constant updates and improvements to smart contract security. It is essential for developers and users to stay informed about the latest developments and best practices to protect their assets and investments.
- Programming errors in smart contract code
- Risks associated with the decentralized nature of smart contracts
- Challenges related to the immutability of smart contracts
- Uncertainty and evolving risks in blockchain technology
An Overview of Smart Contracts
In recent years, smart contracts have emerged as a revolutionary technology that has the potential to transform various industries. A smart contract is a self-executing contract with the terms of the agreement directly written into code. These contracts are powered by blockchain technology, which ensures transparency, security, and immutability.
One of the main advantages of smart contracts is their ability to eliminate the need for intermediaries and reduce transaction costs. Traditional contracts often require lawyers, brokers, and other intermediaries to facilitate and enforce agreements. Smart contracts, on the other hand, automatically execute actions once certain conditions are met, removing the need for intermediaries and reducing costs.
Smart contracts can be used in a wide range of applications, from financial services to supply chain management. For example, in the financial industry, smart contracts can automate various processes such as loan agreements, insurance claims, and asset transfers. In supply chain management, smart contracts can track the movement of goods, verify authenticity, and ensure compliance with regulations.
However, while smart contracts offer many benefits, they also come with their own set of vulnerabilities. The decentralized and transparent nature of blockchain technology makes it difficult to modify or reverse transactions. This means that if a bug or vulnerability is present in a smart contract, it can be exploited by malicious actors without any possibility of recovery.
Therefore, it is crucial to thoroughly analyze and test smart contracts to uncover any vulnerabilities or weaknesses before deployment. This process, known as smart contract auditing, involves reviewing the code for potential security flaws and conducting comprehensive testing to ensure the contract behaves as intended.
In conclusion, smart contracts have the potential to revolutionize various industries by offering transparency, security, and cost savings. However, it is essential to be aware of the vulnerabilities associated with smart contracts and take appropriate measures to mitigate risks. By conducting thorough audits and implementing best practices, we can harness the power of smart contracts while minimizing the likelihood of exploitation.
Definition and Functionality
Smart contracts are self-executing contracts with the terms of the agreement directly written into lines of code. These contracts are stored on a blockchain, a decentralized and transparent digital ledger. The functionality of smart contracts is to automate and enhance the trust and security of transactions between parties, without the need for intermediaries.
Smart contracts use the principles of cryptography to ensure the integrity and immutability of the agreements. They are designed to be tamper-proof and can only be modified by the participants according to the predefined rules. This eliminates the risk of bias or manipulation that is often associated with traditional contracts.
One of the key features of smart contracts is their ability to execute automatically once predetermined conditions are met. They can facilitate various types of transactions such as payments, asset transfers, and data exchanges. This makes them suitable for a wide range of applications including supply chain management, financial services, and decentralized applications (dApps).
Overall, smart contracts provide a secure and efficient way to enforce agreements without relying on a centralized authority. They bring transparency, cost savings, and improved trust to transactions. However, it is important to note that vulnerabilities in the code or the underlying blockchain can pose risks to the integrity and security of smart contracts. Therefore, thorough auditing and testing is necessary to ensure the reliability of smart contracts before they are deployed.
For developers and organizations looking to build and deploy smart contracts, there are platforms and tools available such as free Galxe (GAL) that offer features for testing, monitoring, and securing smart contracts. These resources can help to identify and address vulnerabilities, minimizing the risks associated with smart contract development and deployment.
Benefits and Use Cases

Smart contracts offer numerous benefits and provide a wide range of use cases for businesses and individuals alike. Here are some of the key advantages:
Security:
Smart contracts are built on blockchain technology, which ensures that transactions are secure, transparent, and tamper-proof. The decentralized nature of the blockchain makes it extremely difficult for hackers to manipulate or compromise smart contracts.
Efficiency:
Smart contracts automate and streamline various business processes, eliminating the need for intermediaries and reducing the time and costs associated with manual paperwork. By removing middlemen, smart contracts enable faster and more efficient transactions.
Cost savings:
By eliminating the need for intermediaries and reducing the chances of fraud and errors, smart contracts can significantly reduce costs for businesses. Without the need for legal and administrative fees, businesses can save both time and money.
Transparency:
Smart contracts are stored on a public blockchain, which means that all parties involved can view and verify the terms of the contract. This transparency helps to build trust between parties and reduces the chances of disputes.
Decentralization:
Smart contracts are executed on a decentralized network, removing the need for a centralized authority to oversee transactions. This decentralization eliminates the single point of failure and makes the system more resilient against attacks or outages.
Use cases:
Smart contracts can be applied in various industries, such as finance, supply chain management, real estate, insurance, and more. They can automate processes like payment settlements, supply chain tracking, property transfers, and claims processing, bringing efficiency, transparency, and security to these sectors.
In conclusion, smart contracts offer numerous benefits and have the potential to revolutionize many industries. Their secure, efficient, and transparent nature makes them a valuable tool for businesses and individuals looking to streamline processes and reduce costs.
Common Vulnerabilities
Smart contracts, like any other software, are not immune to vulnerabilities. In fact, due to their decentralized nature and the lack of governance in the blockchain ecosystem, they can be even more exposed to security risks. Here are some common vulnerabilities that have been identified:
- Reentrancy: This vulnerability occurs when a contract allows an external contract to make reentrant calls, enabling malicious contracts to repeatedly call the vulnerable contract before it finishes its execution, resulting in unexpected behavior and potential loss of funds.
- Integer Overflow and Underflow: Smart contracts often handle numerical calculations, and if proper checks are not in place, it can lead to integer overflow or underflow vulnerabilities. Attackers can exploit these vulnerabilities to manipulate values and cause unexpected behavior.
- Unchecked External Calls: Smart contracts can make calls to external contracts or interfaces, and if proper checks and validations are not performed, it can result in vulnerabilities. Attackers can manipulate the behavior of the contract by exploiting the unchecked external calls.
- Timestamp Dependence: The usage of timestamp as a source of randomness or for making critical decisions can be a vulnerability. Attackers can manipulate the timestamp or predict the timestamp to gain an advantage and exploit vulnerabilities in the contract.
- Front-Running: Front-running occurs when a malicious actor sees a transaction being sent to a smart contract and submits a competing transaction with a higher gas price to have their transaction mined before the victim’s transaction. This can be used to exploit the victim’s transaction or manipulate the outcome of the contract.
- Unintended Function Access: Smart contracts often have multiple functions, and if access controls are not implemented correctly, it can lead to unintended function access vulnerabilities. Attackers can exploit these vulnerabilities to perform unauthorized actions or manipulate the contract’s behavior.
These are just a few examples of common vulnerabilities in smart contracts. It is crucial for developers to be aware of these vulnerabilities and implement appropriate security measures to prevent potential exploits and protect users’ funds and data.
Incorrect Programming

One of the major risks associated with smart contracts is the presence of incorrect programming. Since smart contracts are typically written in languages like Solidity, which is relatively new and less mature than traditional programming languages, there is a greater potential for mistakes to occur during the development process. These mistakes can result in vulnerabilities that can be exploited by attackers.
Common errors in smart contract programming include:
- Integer Overflow/Underflow: When performing calculations with integers, it is important to ensure that the result does not exceed the maximum or minimum value that can be represented. Failure to do so can lead to unexpected behavior and possibly vulnerabilities in the contract.
- Reentrancy: Reentrancy occurs when a contract is called again before the previous call has completed. This can be exploited by attackers to manipulate the contract’s state and potentially steal funds.
- Unchecked External Calls: Smart contracts often interact with external contracts or accounts. Failing to properly validate the results of these external calls can introduce risks, such as calling a malicious contract that can manipulate the contract’s behavior.
- Unintended Function Execution: Smart contracts may have unintended functions that can be triggered by attackers. These functions may be leftovers from testing or debugging, but if they are not properly secured, they can be exploited.
It is essential for smart contract developers to thoroughly test their code, perform code reviews, and follow best practices to minimize the risk of incorrect programming. Additionally, there are tools and frameworks available that can help identify potential vulnerabilities and strengthen the overall security of smart contracts.
In conclusion, the presence of incorrect programming poses a significant risk to the security of smart contracts. Developers must be diligent in their coding practices and take proactive measures to identify and mitigate vulnerabilities.
Insufficient Testing
Smart contracts are complex pieces of code that can be difficult to test thoroughly, which can lead to vulnerabilities and exploits.
One issue with testing smart contracts is that they often rely on external data sources, such as oracles, to make decisions. This can make writing comprehensive test cases difficult, as it is impossible to predict all possible inputs from these external sources. As a result, developers may not test certain edge cases or scenarios, leaving room for vulnerabilities to be exploited.
Another challenge is that smart contracts are often written in new and rapidly evolving programming languages, making it difficult to find experienced testers who are familiar with the unique nuances of these languages. This can lead to a lack of expertise and thoroughness in the testing process.
Additionally, smart contracts may interact with multiple external contracts and protocols, further complicating the testing process. Ensuring proper integration and compatibility between different contracts and protocols requires careful testing, but this is often overlooked or not given sufficient attention.
Insufficient testing can also stem from time constraints or lack of resources. Developers may feel pressure to release smart contracts quickly, leading to rushed or incomplete testing. Without thorough and comprehensive testing, vulnerabilities can go undetected and potentially be exploited by attackers.
To address these challenges, it is crucial to invest in thorough testing methodologies and resources. This includes employing experienced testers who are familiar with the unique characteristics of smart contracts and the associated programming languages. Testers should also work closely with developers, auditors, and security experts to identify and address vulnerabilities.
Furthermore, developers should prioritize comprehensive testing, covering all possible scenarios and edge cases, even if it means investing more time and resources. By doing so, developers can reduce the likelihood of vulnerabilities and exploits, making smart contracts more secure and reliable.
External Dependency Risks
Smart contracts rely on a variety of external dependencies, ranging from oracles to external data feeds, to execute their logic. These external dependencies introduce inherent risks that can compromise the security and reliability of the smart contract system.
One of the main risks associated with external dependencies is the possibility of data manipulation or tampering. Since smart contracts often rely on data from external sources, any compromise or manipulation of this data can lead to undesired outcomes and potential loss of funds. For example, if a smart contract uses an external data feed to determine the price of an asset, an attacker could manipulate this data feed to report incorrect prices, leading to incorrect actions being taken by the smart contract.
Another risk is the reliance on centralized services or oracles. Many smart contracts depend on oracles to provide real-world data, such as stock prices or weather information. However, these oracles are often centralized and can be vulnerable to attacks or manipulation. If a malicious actor gains control over the oracle, they can provide false data to the smart contract, leading to unintended consequences.
Furthermore, external dependencies can also introduce performance and scalability issues. Smart contracts that rely on real-time data or frequent updates may experience delays or bottlenecks if the external dependency cannot handle the required volume of requests. This can result in slow transaction times or even contract failures, compromising the overall functionality of the system.
| Risk | Description |
|---|---|
| Data Manipulation or Tampering | External data used by smart contracts can be compromised or manipulated, leading to undesired outcomes. |
| Reliance on Centralized Services or Oracles | Smart contracts relying on centralized oracles are vulnerable to attacks or manipulation by malicious actors. |
| Performance and Scalability Issues | External dependencies may not be able to handle the required volume of requests, leading to delays or contract failures. |
In order to mitigate these risks, it is important to carefully evaluate and select external dependencies for smart contracts. Countermeasures such as data verification, redundancy, and decentralization can be implemented to enhance the security and reliability of smart contract systems.
Exploitation Techniques
Smart contracts are susceptible to various exploitation techniques due to their complexity and the potential for coding errors. In this section, we will explore some of the common ways that attackers can take advantage of vulnerabilities in smart contracts.
Reentrancy Attacks: One common exploitation technique is known as a reentrancy attack. In this type of attack, the attacker exploits a vulnerability in the contract code to repeatedly call the contract’s fallback function before the previous call completes. This can lead to unexpected behavior and allow the attacker to drain the contract’s funds.
Integer Overflow and Underflow: Another commonly exploited vulnerability is integer overflow and underflow. Smart contracts often use integers to handle calculations and store values. If the values are not properly checked and constrained, it can lead to unexpected behavior. Attackers can manipulate these values to their advantage and potentially bypass authorization checks or gain control of the contract’s execution flow.
Timestamp Dependence: Smart contracts often rely on timestamps to make decisions or perform certain actions. However, relying solely on timestamp values can be dangerous, as attackers can manipulate the timing and exploit vulnerabilities. Additionally, timestamps can be influenced by external factors, such as time zone differences or network delays, which can lead to unexpected results.
Unchecked User Inputs: Smart contract developers need to carefully validate and sanitize user inputs to prevent potential exploits. Attackers can provide malicious inputs that can exploit vulnerabilities in the contract’s code or manipulate its state. By failing to validate user inputs, developers increase the risk of potential exploits.
Delegatecall and Callcode: Delegatecall and callcode are low-level functions in the Ethereum Virtual Machine (EVM) that can be used to interact with other contracts. However, if not used correctly, these functions can introduce vulnerabilities. Attackers can exploit improper usage of delegatecall and callcode to gain unauthorized access to functions or manipulate the contract’s storage.
Front-Running: Front-running is a technique where an attacker observes pending transactions and tries to exploit the time gap between the transaction submission and its inclusion in the blockchain. By manipulating the order of transactions or submitting a transaction with higher gas fees, attackers can potentially gain an advantage and exploit vulnerabilities in smart contracts.
Third-Party Libraries and Dependencies: Smart contracts often rely on third-party libraries or dependencies for various functionalities. However, using untrusted or outdated libraries can introduce vulnerabilities. Attackers can exploit vulnerabilities in these libraries to manipulate the contract’s behavior or gain unauthorized access to sensitive information.
Blockchain Reorganizations: Smart contracts are executed on a blockchain, which can undergo reorganizations due to chain splits or forks. During these reorganizations, previously confirmed transactions can become unconfirmed and vice versa. Attackers can exploit these reorganizations to manipulate the execution flow of smart contracts or double-spend tokens.
It is crucial for smart contract developers and auditors to be aware of these exploitation techniques and implement best practices to mitigate the risk of potential vulnerabilities in their code.
Reentrancy Attack

A reentrancy attack is a type of exploit that can occur in smart contracts when a contract calls an external contract and then receives a callback before the first call completes. This vulnerability can be exploited by an attacker to repeatedly call the external contract’s function and manipulate state variables in the calling contract.
The reentrancy attack takes advantage of the fact that in some cases, the state of a contract is not properly updated until the external call is completed. By repeatedly calling the external contract’s function before the state is updated, the attacker can manipulate the state in a way that benefits them.
One example of a reentrancy attack occurred in the infamous “DAO” incident in 2016. The attacker was able to repeatedly call the DAO contract’s “withdraw” function, which resulted in them draining a significant amount of funds from the contract before the contract’s balance was properly updated.
To prevent reentrancy attacks, developers should be careful when calling external contracts and ensure that all state updates are performed before making any external calls. They can also use mutex locks or other synchronization mechanisms to prevent reentrancy attacks.
DoS Attack
A Denial-of-Service (DoS) attack is a type of cyber attack that aims to make a computer system or network unavailable to its intended users by overwhelming it with a flood of illegitimate requests or by exploiting a vulnerability in the system. In the context of smart contracts, a DoS attack can be used to disrupt the normal operation of a contract and prevent it from executing its intended functions.
The vulnerability that can be exploited in a smart contract to carry out a DoS attack can vary, but it often involves manipulating the contract’s code or its execution environment in such a way that it causes the contract to consume excessive resources, such as gas, computation power, or storage. This can result in the depletion of these resources, making it impossible for other legitimate users to interact with the contract.
There are several ways in which a smart contract can be specifically targeted for a DoS attack:
- Reentrancy attacks: These attacks exploit the reentrancy vulnerability in a contract, where an external malicious contract can invoke a vulnerable contract repeatedly in a loop, exhausting its resources.
- Gas limit attacks: These attacks attempt to consume all the gas allocated to a contract’s execution, preventing it from completing its intended functions.
- State manipulation attacks: These attacks exploit vulnerabilities in the contract’s state manipulation logic, causing the contract to enter an infinite loop or to consume excessive resources.
Protecting against DoS attacks in smart contracts requires careful design and implementation. Contract developers should thoroughly review and test their code to identify and fix any vulnerabilities that could be exploited. Additionally, contract designs should include mitigation strategies such as gas limits, timeouts, and checks on resource consumption to prevent excessive resource usage by malicious actors.
By understanding and addressing the vulnerabilities that can lead to DoS attacks, developers can ensure the resilience and availability of their smart contracts in the face of potential threats.
Overflow Attacks

Overflow attacks are one of the most common types of vulnerabilities found in smart contracts. They occur when an attacker is able to input a value that exceeds the maximum limit defined by the contract, causing an overflow and potentially leading to unexpected behavior or even loss of funds.
There are two main types of overflow attacks: integer overflow and buffer overflow.
An integer overflow occurs when a number exceeds the maximum value that can be represented in computer memory. This can lead to unexpected results, such as returning to a negative value instead of the expected positive value, or causing the contract’s logic to malfunction.
A buffer overflow, on the other hand, occurs when a program tries to write data outside the bounds of a fixed-size buffer. This can be exploited by an attacker to overwrite important data or execute arbitrary code.
Overflow attacks can be prevented by implementing proper input validation and using secure programming practices. This includes checking for overflow conditions and bounds checking to ensure that values stay within the expected ranges.
Furthermore, it is important for smart contract developers to properly test their contracts and conduct security audits to identify and fix any vulnerabilities before deploying them on the blockchain.
In conclusion, overflow attacks can have serious consequences for smart contracts, leading to unexpected behavior and potential loss of funds. It is crucial for developers to be aware of these vulnerabilities and take appropriate measures to prevent them.
FAQ:
What are smart contracts?
Smart contracts are self-executing contracts with the terms of the agreement directly written into lines of code. They automatically execute and enforce the agreements without the need for intermediaries.
What are the benefits of using smart contracts?
Smart contracts offer various benefits, including increased efficiency, transparency, and security. They eliminate the need for third-party intermediaries, reduce costs, and provide a tamper-proof and immutable record of transactions.
What are the vulnerabilities of smart contracts?
Smart contracts can be vulnerable to various risks, such as coding errors, implementation flaws, and malicious attacks. These vulnerabilities can lead to financial losses, contract failures, and unauthorized access to sensitive information.
How can coding errors impact smart contracts?
Coding errors in smart contracts can have serious consequences. They can create vulnerabilities that allow attackers to exploit the contract and steal funds or manipulate the contract’s behavior. Additionally, coding errors can lead to unpredictable or unintended outcomes, potentially causing financial losses.